'GODLESS' Android Mobile Malware Uses Multiple Exploits to Root Devices
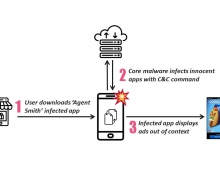
Researchres at Trendmicro have came across a family of mobile malware called Godless (detected as ANDROIDOS_GODLESS.HRX) that has a set of rooting exploits in its pockets. By having multiple exploits to use, Godless can target virtually any Android device running on Android 5.1 (Lollipop) or earlier. According to Trendmicro, almost 90% of Android devices are currently running on affected versions. Based on the data gathered from the Trend Micro Mobile App Reputation Service, malicious apps related to this threat can be found in prominent app stores, including Google Play, and has affected over 850,000 devices worldwide, with almost half in India and more in other southeast Asian countries. Less than 2 percent were in the U.S.
Godless is reminiscent of an exploit kit, in that it uses an open-source rooting framework called android-rooting-tools. The said framework has various exploits in its arsenal that can be used to root various Android-based devices.
In addition, with root privilege, the malware can then receive remote instructions on which app to download and silently install on mobile devices. This can then lead to affected users receiving unwanted apps, which may then lead to unwanted ads. Even worse, these threats can also be used to install backdoors and spy on users.
A newer variant can also bypass security checks at app stores like Google Play. Once the malware has finished its rooting, it can be tricky to uninstall, the security firm said.
Trend Micro said it found various apps in Google Play that contain the malicious code.
"The malicious apps we’ve seen that have this new remote routine range from utility apps like flashlights and Wi-Fi apps, to copies of popular game," the company said.
Some apps are clean but have a corresponding malicious version that shares the same developer certificate. The danger there is that users install the clean app but are then upgraded to the malicious version without them knowing.
"When downloading apps, regardless if it’s a utility tool or a popular game, users should always review the developer. Unknown developers with very little or no background information may be the source of these malicious apps," Trend said.
It's also best to download apps from trusted stores such as Google Play and Amazon, it says. And of course, Trend recommends you buy some mobile security software.