Firefox Extension Steals Facebook, Twitter, Sessions
A Firefox extension called "Firesheep" was presented today at Toorcon 12, demontrating how easy it is for attackers to access accounts belonging to other users on the same network.
When logging into a website, users usually start by submitting their username and password. The server then checks to see if an account matching this information exists and if so, replies back to them with a "cookie" which is used by the browser for all subsequent requests.
It's extremely common for websites to protect users' password by encrypting the initial login, but surprisingly uncommon for websites to encrypt everything else. This leaves the cookie (and the user) vulnerable. HTTP session hijacking (sometimes called "sidejacking") is when an attacker gets a hold of a user's cookie, allowing them to do anything the user can do on a particular website. On an open wireless network, cookies are basically shouted through the air, making these attacks extremely easy.
This is a widely known problem that has been talked about to death, yet very popular websites continue to fail at protecting their users. The only effective fix for this problem is full end-to-end encryption, known on the web as HTTPS or SSL. Facebook is constantly rolling out new "privacy" features in an endless attempt to quell the screams of unhappy users, but what's the point when someone can just take over an account entirely? Twitter forced all third party developers to use OAuth then immediately released (and promoted) a new version of their insecure website. When it comes to user privacy, SSL is the elephant in the room.
Firesheep is a Firefox extension designed to demonstrate just how serious this problem is.
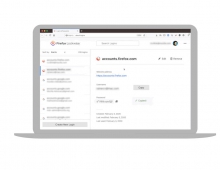
According to the demontration, after installing the extension, a new sidebar appears on Mozilla's Firefox browser. After connecting to any open wifi network. As soon as anyone on the network visits an insecure website known to Firesheep, their name and photo will be displayed. By double-clicking on someone, and you're instantly logged in as them.
Firesheep is free, open source, and is available now for Mac OS X and Windows, with Linux support to be on the way.
It's extremely common for websites to protect users' password by encrypting the initial login, but surprisingly uncommon for websites to encrypt everything else. This leaves the cookie (and the user) vulnerable. HTTP session hijacking (sometimes called "sidejacking") is when an attacker gets a hold of a user's cookie, allowing them to do anything the user can do on a particular website. On an open wireless network, cookies are basically shouted through the air, making these attacks extremely easy.
This is a widely known problem that has been talked about to death, yet very popular websites continue to fail at protecting their users. The only effective fix for this problem is full end-to-end encryption, known on the web as HTTPS or SSL. Facebook is constantly rolling out new "privacy" features in an endless attempt to quell the screams of unhappy users, but what's the point when someone can just take over an account entirely? Twitter forced all third party developers to use OAuth then immediately released (and promoted) a new version of their insecure website. When it comes to user privacy, SSL is the elephant in the room.
Firesheep is a Firefox extension designed to demonstrate just how serious this problem is.
According to the demontration, after installing the extension, a new sidebar appears on Mozilla's Firefox browser. After connecting to any open wifi network. As soon as anyone on the network visits an insecure website known to Firesheep, their name and photo will be displayed. By double-clicking on someone, and you're instantly logged in as them.
Firesheep is free, open source, and is available now for Mac OS X and Windows, with Linux support to be on the way.