Facebook, Mozilla, and Cloudflare Announce TLS Delegated Credentials Standard to Improve Security of TLS Certificates
Facebook, Mozilla, and Cloudflare announced today a new technical specification called TLS Delegated Credentials, currently undergoing standardization at the Internet Engineering Task Force (IETF).
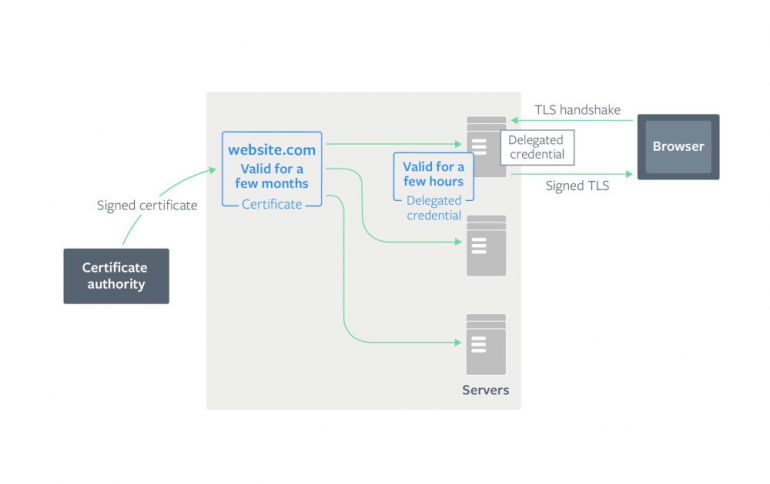
Delegated credentials is an extension to the TLS protocol, and an extremely effective method for securing certificates. TLS is a cryptographic protocol that underpins the more widely-known HTTPS protocol, used for loading websites inside browsers via an encrypted connection.
In modern server deployments, a certificate could be deployed to thousands of servers, which could be distributed all over the world. It’s important to ensure the security of the certificate to prevent potential attackers from gaining control of a certificate, which would enable them to perform a man-in-the-middle (MITM) attack on traffic to the server.
If a certificate becomes compromised before it expires, the only option currently available to server operators is to revoke the certificate. However, certificate revocation does not work well for modern browsers. Revocation checking mechanisms such as Online Certificate Status Protocol (OCSP) may require browsers to speak to a certificate authority and can be blocked. They can also add latency to the connection establishment. As a result, modern browsers do not rely on them and instead use alternative mechanisms, such as the CRLsets used by Chrome. The truth is that the shorter the certificate lifetime, the less likely a certificate will need to be revoked before it expires. However, if the certificate expiration time is reduced to just a few hours, and in case the network between the authority that validates the certificates and servers is temporarily down, will also result in a server not being able to obtain a valid certificate. Without a valid certificate, the website will go down. To mitigate this risk, services like Facebook's generally opt for a longer expiration time, so there is time to recover from any failures.
Delegated credentials allow a server to better balance this trade-off between security and reliability. A server generates a new delegated credential structure containing a public key and an expiration time, which can be as little as a few hours. It can then use its signed certificate (also known as a leaf certificate) to sign the delegated credential. Since this delegated credential is generated and signed by a server, it does not need to contact the certification authority servers every time it needs to create a new delegated credential.
The delegated credentials can live up to seven days and can be rotated automatically once they expire.
The TLS Delegate Credentials extension was specifically developed for large website setups, such as Facebook, or for website using content delivery networks (CDNs), such as Cloudflare.
TLS Delegated Credentials will be compatible with the TLS protocol v1.3 and later.





















