WhatsApp And Telegram Flaw Puts Users At Risk
A new research by Symantec reveals a Media File Jacking flaw affecting WhatsApp and Telegram for Android.
WhatsApp and Telegram media files could be manipulated by malicious actors according to Symantec’s Modern OS Security team. The security flaw, dubbed “Media File Jacking”, affects WhatsApp for Android by default, and Telegram for Android if certain features are enabled. It stems from the lapse in time between when media files received through the apps are written to the disk, and when they are loaded in the apps’ chat user interface (UI) for users to consume. This critical time lapse presents an opportunity for malicious actors to intervene and manipulate media files without the user’s knowledge. If the security flaw is exploited, a malicious attacker could misuse and manipulate sensitive information such as personal photos and videos, corporate documents, invoices, and voice memos. Attackers could take advantage of the relations of trust between a sender and a receiver when using these IM apps for personal gain or to wreak havoc.
The threat is concerning in light of the common perception that the new generation of IM apps is immune to content manipulation and privacy risks, thanks to the utilization of security mechanisms such as end-to-end encryption. Users generally trust IM apps such as WhatsApp and Telegram to protect the integrity of both the identity of the sender and the message content itself. However, no code is immune to security vulnerabilities. While end-to-end encryption is an effective mechanism to ensure the integrity of communications, it isn’t enough if app-level vulnerabilities exist in the code. The researchers found demonstrates is that attackers may be able to successfully manipulate media files by taking advantage of logical flaws in the apps, that occur before and/or after the content is encrypted in transit.
By default, WhatsApp stores media files received by a device in external storage, in the following path: /storage/emulated/0/WhatsApp/Media/. In Telegram, if a user enables the “Save to Gallery” feature, under the assumption that this is safe and without understanding its indirect ramifications, Telegram will similarly store files in: /storage/emulated/0/Telegram/. Both are public directories. The apps load the received files from the public directories for users to see in the chat interface, when they enter the relevant chat.
The fact that files are stored in, and loaded from, external storage without proper security mechanisms, allows other apps with write-to-external storage permission to risk the integrity of the media files.
The researchers found that in the time between when files are first received on a device and written to the disk, and when they are loaded for users to consume via the apps, the ideal opportunity for exploitation arises: malware can instantaneously analyze and manipulate the files (or just replace them with the attacker’s chosen files) for malicious gain.
Additionally, data can be manipulated on WhatsApp both when sending files - meaning the attack is launched on the sender’s device - and when receiving files - with the attack happening on the receiving device.
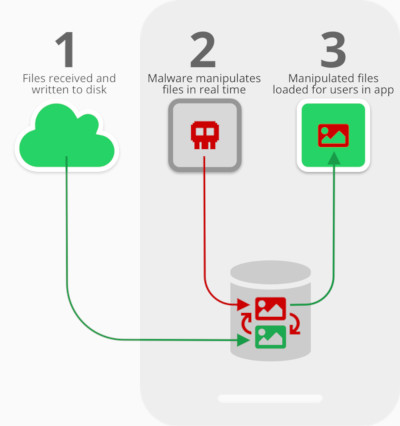
The researchers proved that an app downloaded by a user can manipulate personal photos in near-real time and without the victim knowing. The app runs in the background and performs a Media File Jacking attack while the victim uses WhatsApp. It monitors for photos received through the IM app, identifies faces in the photos, and replaces them with something else, such as other faces or objects.
In one of the most damaging Media File Jacking attacks, a malicious actor could manipulate an invoice sent by a vendor to a customer, to trick the customer into making a payment to an illegitimate account.
An attacker could also exploit the relations of trust between employees in an organization. A CEO sends his CFO an audio message, via WhatsApp, requesting updated slides for a board meeting next week. The attacker, using voice reconstruction via deep learning technology – something that is becoming more and more feasible today – alters the original audio file to communicate to the CFO, in the CEO’s own voice, that a payment needs to be transferred immediately to a fictitious party, which is in fact the attacker. The bad actor not only manipulates the communications of the CEO, but goes a step further to reconstruct his voice, resulting in a very effective deception technique. The original message from the CEO is replaced when it arrives at the CFO’s phone. What the CFO hears in the end is a credible audio message from his boss to make a payment, something that can easily be perceived as a legitimate request by an unaware employee.
To ensure that media files are kept safe from malicious actors, Symantec recommends the following measures:
- Validate the integrity of files: Store in a metadata file a hash value for each received media file before writing it to the disk. Then, confirm that the file has not been changed (i.e. the hash is the same) before the media file is loaded by the app in the relevant chat portion for users to see. This step can help developers validate that files were not manipulated before they are loaded. This approach balances between the security (protection against Media File Jacking attacks) and functionality (e.g., supporting third party backup apps) needs of the IM apps.
- Internal storage: If possible, store media files in a non-public directory, such as internal storage. This is a measure some IM apps have chosen.
- Encryption: Strive to encrypt sensitive files, as is usually done for text messages in modern IM solutions. This measure, as well as the previous one, will better protect files from exposure and manipulation. The downside is that other apps, such as photo backup apps, won’t be able to easily access these files.
With the release of Android Q, Google plans to enact changes to the way apps access files on a device’s external storage. Android’s planned Scoped Storage is more restrictive, which may help mitigate threats. Scoped Storage means that apps will have their own storage area in an app-specific directory, but will be prevented from accessing files in the entire storage partition, unless an explicit permission is granted by the user.
Symantec notified Telegram and Facebook/WhatsApp about the Media File Jacking vulnerability.
WhatsApp responded to the disclosure, saying that the company "had looked closely at this issue and it’s similar to previous questions about mobile device storage impacting the app ecosystem. WhatsApp follows current best practices provided by operating systems for media storage and looks forward to providing updates in line with Android’s ongoing development. The suggested changes here could both create privacy complications for our users and limit how photos and files could be shared."
IM app users can mitigate the risk Media File Jacking by disabling the feature that saves media files to external storage. Android's WhatsApp and Telegram users can check (and change) their settings to ensure media files are not saved to external storage. For WhatsApp this is done in "Settings -> Chats -> Media Visibility," and for Telegram in "Settings -> Chat Settings -> Save to Gallery." Given the exposure this hack has now been given, the risk has become more real. And so it would seem sensible to check and change those settings now.