
Microsoft Azure Confidential Computing Adds Cloud Security to Keep Out Hackers
Microsoft and Intel are offering a new cloud-computing service with more powerful encryption to secure data from hackers and government snoops.
Azure confidential computing offers a protection that to date has been missing from public clouds, encryption of data while in use. The Azure team, along with Microsoft Research, Intel, Windows, and Microsoft's Developer Tools group, have been working on confidential computing software and hardware technologies for over four years.
The service, now available to Microsoft's customers via an Early Access program, protects Microsoft Azure clients from malicious insiders with administrative privilege or direct access to hardware on which it is being processed. It also protects data against hackers and malware that exploit bugs in the operating system, application, or hypervisor, and of course any third parties accessing it without their consent.
Confidential computing ensures that when data is "in the clear," which is required for efficient processing, the data is protected inside a Trusted Execution Environment (TEE - also known as an enclave), an example of which is shown in the figure below.
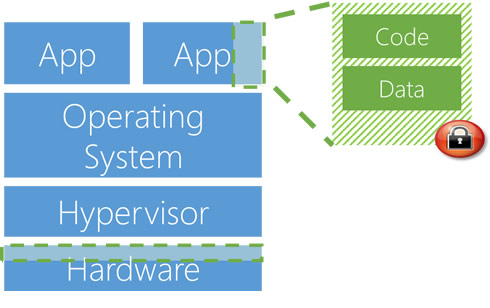
A virtual enclave is essentially a black box that keeps anyone outside the customer -- including Microsoft itself -- from accessing the data. TEEs ensure there is no way to view data or the operations inside from the outside, even with a debugger. They even ensure that only authorized code is permitted to access data. If the code is altered or tampered, the operations are denied and the environment disabled. The TEE enforces these protections throughout the execution of code within it.
Azure confidential computing will offer two ways to create these secure enclaves. One is based on Microsoft's own server software, while the other uses Intel chips with that company's built-in security features, according to Azure Chief Technology Officer Mark Russinovich.
Initially Microsoft supports two TEEs, Virtual Secure Mode and Intel SGX. Virtual Secure Mode (VSM) is a software-based TEE that's implemented by Hyper-V in Windows 10 and Windows Server 2016. Hyper-V prevents administrator code running on the computer or server, as well as local administrators and cloud service administrators from viewing the contents of the VSM enclave or modifying its execution. Microsoft is also offering hardware-based Intel SGX TEE with the first SGX-capable servers in the public cloud.
Microsoft already uses enclaves to protect everything from blockchain financial operations, to data stored in SQL Server, and its own infrastructure within Azure. While the company has previously spoken about its confidential computing blockchain efforts, known as the Coco Framework, Microsoft today announced
the use of the same technology to implement encryption-in-use for Azure SQL Database and SQL Server. This is an enhancement of Microsoft's Always Encrypted capability, which ensures that sensitive data within a SQL database can be encrypted at all times without compromising the functionality of SQL queries. Always Encrypted achieves that this by delegating computations on sensitive data to an enclave, where the data is safely decrypted and processed.
Microsoft's customers can try out Azure confidential computing through an Early Access program, which includes access to Azure VSM and SGX-enabled virtual machines, as well as tools, SDKs, and Windows and Linux support to enable any application in the cloud to protect its data while in use.
The new service means that Microsoft won't have the capability to turn over data in response to government warrants and subpoenas, an issue at the heart of a current Microsoft lawsuit against the U.S. government fighting the requirement to turn over client data, sometimes without the customer's knowledge.
Google has been working on its own chips, called Titan, that offer a different type of security against hackers in cloud networks. That effort makes sure that when machines boot up, every piece of Google software is valid and hasn't been tampered with.




















