Elby CloneCD CD-R Software
2. CD-Protections Overview
Review Pages
2. CD-Protections Overview
3. Copy Protection Detectors
4. Add-ons Patchers
5. Interface - Options (1)
6. Interface - Options (2)
7. Various Protection Tests - Page 1
8. Various Protection Tests - Page 2
9. Various Protection Tests - Page 3
10. Tests Conclusion
11. Final Conclusion
12. FAQ
13. Hardware Suggestions
14. Tips
15. Future Plans
CloneCD Guide - Page 2
CD-Protections Overview
1) SafeDisc
- How it works:
The SafeDisc is comprised of three key features: (1) an authenticating digital
signature, (2) encryption that protects the content, and (3) anti-hacking software.
When attempting to make an unauthorized copy with a CD-R or with professional
mastering equipment, the digital signature is not transferred to the copy. When
an unauthorized copy is played back, the absence of the signature will prevent
decryption of the program and the copy will not play.
 -
How to recognize it:
-
How to recognize it:
This protection is very visible in 2 ways:
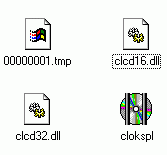
- every CD protected will always have at least a file called "0000001.tmp"
and most of the time also these files: clocksp.exe , .iCD file , CLCD16.DLL,
CLCD32.DLL. File named "clocksp.exe" also have specific icon.
- This type of CD includes lots of unreadable error . It usually have about
10000 unreadable sectors (usually start at sector 800+ and end at 10000+, see
test for details) which represents about 20 Mb in fact.
SafeDisc v2.0
Macrovision at 18 of August 2000 posted the press release for SafeDisc v2.0.
What's New?
o API support - the SAFEDISC toolkit includes an API that will allow publishers to extend the SAFEDISC security to encrypt various functions contained in their content.
o New architecture - major re-architecture of the SAFEDISC code to disable automated hacking tools and to include additional encryption to delay hacking.
o Disc burning prevention - introduction of additional digital signatures to improve resistance against copying.
o Fail-safe manufacturing - assures that SAFEDISC masters will only be mastered on SAFEDISC-enabled production lines.
- How it works:
The first game, which includes the new SafeDisc v2.0 protection, is Red Alert
2. People have reported that you can easily copy the CD BUT it will won't run
it most CD-ROM/CDR-W drives!! If you try to install it you will get an error
during the setup process (error in .tmp file). You can read the technical background
at this page.
- How to recognize it: The .icd file (the SafeDisc loader) is gone; the loader is now integrated in the exe files (in case of RA2 in the game.exe AND the setup.exe) and has nearly doubled in size. The bad sectors are less (10051) than in SafeDisc 1 (10141) protected CDs.
2) SecuROM
- How it works:
It is the combination of an electronic fingerprint applied to each disc and
a sophisticated encryption technology for authentication differentiating a legitimate
CD-ROM from a pirated disc. Unlike SafeDisc protection , the SecuROM protection
does not rely on the deliberate introduction of unreadable errors onto the disc;
consequently: any CD-Reader supporting RAW reading (and ability to read SubChannel)
can do the job in a fast way.
- How to recognize it:
Most of the time, theses following files can be found on that type of CD : CMS16.DLL,
CMS_95.DLL or CMS_NT.DLL ; but you may find CD protected with SecuROM that don't
contain theses files.
So, another way to reckon it is to look at the barcode of CD ,
you will be able to distinguish a little "logo" with name "DADC"
on it , (it only ![]() applies
with Data CD since AudioCDs pressed by Sony also include this logo) (e.g "Hachette
2000 Encyclopedie" is a French SecuROM protected CD that only contains
"DADC" logo).
applies
with Data CD since AudioCDs pressed by Sony also include this logo) (e.g "Hachette
2000 Encyclopedie" is a French SecuROM protected CD that only contains
"DADC" logo).
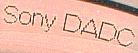 Update:
Recently Sony updated the SecuROM protection in order to make it much more difficult
to duplicate. The game Vrally 2 Expert-Edition uses that new protection. This
time the protection checks for CDR media and when finds it crashes the application.
CloneCD latest builds can duplicate the new SecuROM but you need to install
the backup only from CD-ROMs!
Update:
Recently Sony updated the SecuROM protection in order to make it much more difficult
to duplicate. The game Vrally 2 Expert-Edition uses that new protection. This
time the protection checks for CDR media and when finds it crashes the application.
CloneCD latest builds can duplicate the new SecuROM but you need to install
the backup only from CD-ROMs!
3) LaserLock
- How it works:
LaserLock uses a combination of encryption software and unique laser marking
on the CD surface made during the special LaserLock glass mastering procedure,
in order to make copying virtually impossible. Every CD-ROM application has a unique locking parameter that provides a complete
protection against illegal re-mastering and reproduction.
Every CD-ROM application has a unique locking parameter that provides a complete
protection against illegal re-mastering and reproduction.
- How to recognize it:
There is always a hidden directory called "LaserLock" at the root
of the CD, this directory usually contains few files that are full of unreadable
sector. Moreover , a little thin circle containing theses unreadable sectors
can be seen on the CD.
5) LibCrypt protection
LibCrypt sounds like a magical word for SONY ? or should I have said "sounded"
:) since this protection is also bypassed thanks to CloneCD. As CloneCD author
said: "..This is a nice "side effect" since CloneCD is originally
designed for backing up PC CD.."
This protection has been introduced in October 98 with the release of the game MediEvil , the protection uses a Digital ID which is stored in the SubChannel , it consists in a 16Bit key. Like SafeDisc protection, Libcrypt have have evolved in the time and there are currently 4 versions of LIBCRYPT called LC-1 , LC-2 , LC-3 ,LC-4: this one is in fact based on LC-3 scheme but includes extra routines and several ".exe" file , it makes the debugging work harder for the cracker, but for CloneCD: it is as easy as previous Libcrypt protections since this protection is always stored in the SubChannel Data and CloneCD copies everything it can find :-)
- How it works:
As with any other type of protection, LibCrypt is composed of two separate routines:
The first one performs a control check on the disk to discover if it is a copy,
the second, based on the result of the first one, decrypts a block of data and
crashes the PSX in the case of an incorrect result. Although based on the same
code, the two routines have been altered a few times, to the point that in the
last evolution (LC3) they have very little in common with the initial basic
code.
- How to recognize it:
There's no official way , in fact you need to play the backup until you see
the game crashes !
There is in fact a little alternative way: A nice tool has been made by Icarus/Paradox (with initial idea from AVH) in order to find the right key (used as a parameter for subroutines) faster, you need to put the LC-F CD (Libcrypt finder) in your Playstation, insert the original protected CD or cloned CD in the Playstation, then the 16Bit key appears on the screen in few seconds: all non protected game will always display this value : $1F0000045 ;therefore : every value different than the one mentioned will mean that the game is Libcrypt protected . Don't expect to find this tool over the net since it is only aimed to Paradox members, you can at least visit their website at www.paradogs.com :-)
Another useful info: Infogrames (video games editor) is known to be the firm who has officially bought Libcrypt License from Sony, therefore, since End of June 99 : 80% of games released by Infogrammes have been protected (e.g V-Rally 2 , Le Mans 24H , Eagle One Harrier Attack ...etc...Gekido)
6) CD-COPS
- How it works:
CD-Cops is a shell protection which is added to the CD's main executable. This
is the only change necessary. Minute differences are measured to establish the
CD-ROM's fingerprint and to ensure that copies are not accepted. This fingerprint
is expressed as an 8-digit code or key number.
- How to recognize it :
The file CDCOPS.DLL can be found in the installation director and also Files
with the .GZ_ and .W_X extensions.
7) DiscGuard
- How it works:
DiscGuard is an anti-piracy technology for optical media that works by putting
a "signature" onto a glass master during mastering, using a specially
enhanced mastering machine, or onto a CD-R via DG-Author, a forthcoming product
(Q3 '99) consisting of a specially enhanced CD-R recorder with proprietary software.
- How to recognize it:
Theses files : IOSLINK.VXD and IOSLINK.SYS can be found on CD or Installation
directory
Review Pages
2. CD-Protections Overview
3. Copy Protection Detectors
4. Add-ons Patchers
5. Interface - Options (1)
6. Interface - Options (2)
7. Various Protection Tests - Page 1
8. Various Protection Tests - Page 2
9. Various Protection Tests - Page 3
10. Tests Conclusion
11. Final Conclusion
12. FAQ
13. Hardware Suggestions
14. Tips
15. Future Plans













